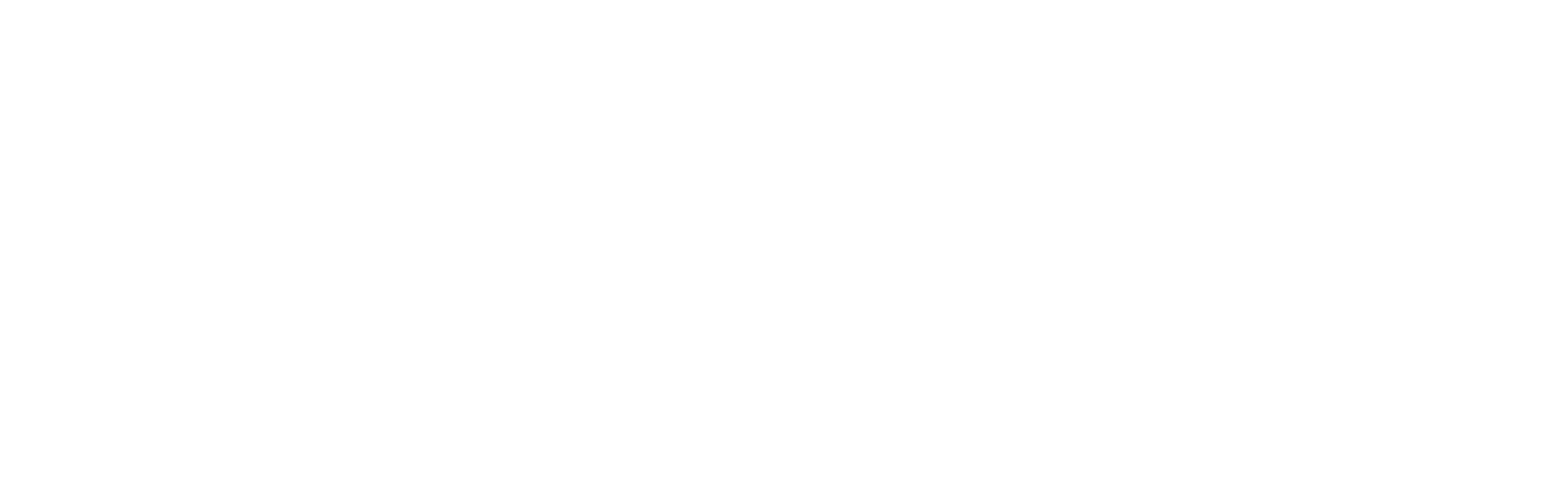Information Security
Security Operations: SecOps and SOC
Security operations can vary significantly from company to company, differing greatly in size and maturity. Whether security functions are a simple incident management device or full-fledged mission control centers with the highest levels of protection, they all share the same goal: preventing, identifying, and mitigating threats to the organization.

While cybersecurity teams continue to evolve thanks to new technologies and philosophies, it’s important to understand the conceptual differences between SecOps and SOC, and how they can work together for the modern enterprise.
What is SecOps?
Security Operations (SecOps) is the combination of IT security and IT operations to effectively mitigate risks. SecOps team members jointly assume responsibility and ownership of any security concerns, ensuring that security is embedded throughout the operations lifecycle.
Historically, security and operations teams often had different and conflicting business goals. Operations teams focused on building systems to achieve performance and uptime goals, while security teams concentrated on meeting regulatory requirements, implementing defenses, and addressing security concerns.
The downside of this model is that security was treated as something to “deal with later,” often viewed as a burden that slowed down operations and created overhead. However, as threats have continued to grow in sophistication, many organizations recognize that this past environment no longer meets the needs of modern business.
By adopting an integrated SecOps team within the development team, Looplex has embedded security throughout the operations process from the beginning. Addressing security from the “ground up” ensures that we meet requirements and design systems with security in mind. This “shift-left” mindset enables security to work cohesively in system configuration while challenging operations team members to adjust how they build and develop solutions on our platform.
What is SOC?
A Security Operations Center (SOC) is a group of security professionals working together to:
- Identify and proactively mitigate security risks to the organization.
- Defend against any security breaches.
In the past, a SOC was a physical facility with massive cybersecurity protections. Within a SOC, the team monitored security statistics and alerts. Our SOC, like those of other cloud-first architecture companies, is fully virtual, but the roles and responsibilities of the SOC have not changed.
For SOCs following best practices, some of their expected responsibilities include:
- Ensuring compliance.
- Penetration testing.
- Architectural planning.
- Vulnerability testing.
- Threat intelligence.
- Analyzing log and event data.
- Identifying and responding to incidents.
- Identity and access management.
- Key management.
- Firewall administration.
- Endpoint management.
It’s easy to imagine that teams often become overwhelmed due to massive data loads, skill shortages, increasing remote teams, and security concerns. However, by incorporating modern methodologies, our security team has begun sharing responsibilities with other company members, enhancing their ability to proactively identify risks and mitigate threats.
Integrating SecOps into SOC
SecOps itself is a set of processes, tools, and SOC practices that help businesses achieve their security goals more successfully and efficiently. However, the classic SOC is not compatible with the SecOps culture. Historically, SOCs operated completely isolated from the rest of the organization, performing specific functions with little interaction with other business areas.
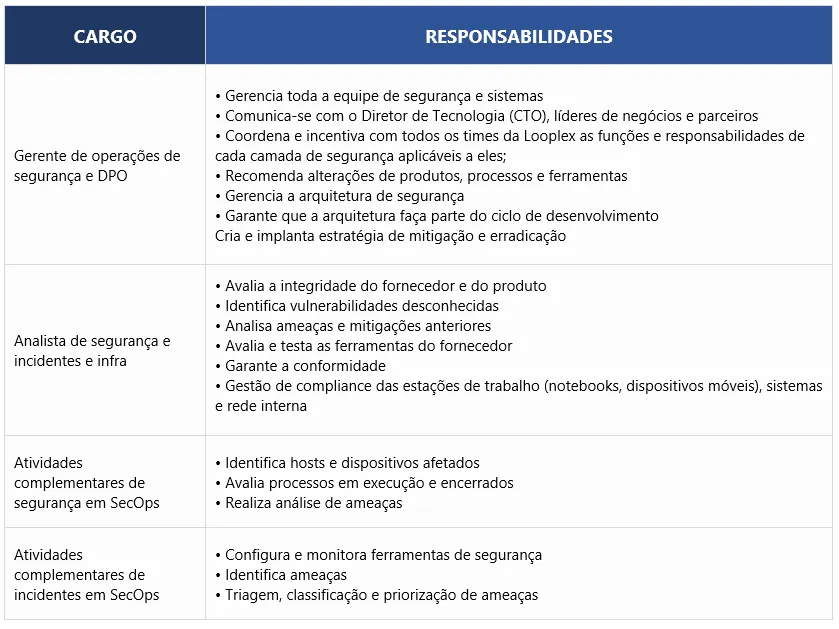
Today, security must be a collaborative effort. A modern SOC promotes collaboration and communication between operations and security teams, which is why we have integrated security into IT and development processes.
At Looplex, we have distributed the SOC by (a) removing security from its silo and spreading responsibilities across departments, (b) establishing a culture of collaboration by opening the SOC and CSIRT to any member whose functions impact security, and (c) creating study groups and best practices with selected team members.
More than that, at Looplex, we have incorporated the SOC and SecOps directly into development, turning our team into DevSecOps.
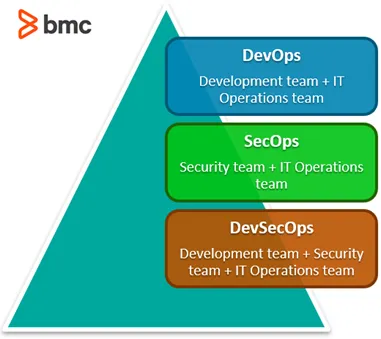
SecOps and DevSecOps offer ways to embed security throughout the product lifecycle.
SOC vs. CSIRT: What’s the difference?
In the world of security operations, terms like CSIRT, CIRT, CERT, and CIRC are often mentioned alongside the SOC. In summary, the first four are generally considered synonyms describing teams focused on incident response, while the SOC typically has a broader scope encompassing digital or cybersecurity.
Understanding the terminology helps avoid misunderstandings that could hinder planning and best practices adoption efforts.
CSIRT, CIRT, CERT, and CIRC
- CSIRT stands for Computer Security Incident Response Team.
- CERT means Computer Emergency Response (or Readiness) Team.
- CIRT is used as Computer Incident Response Team or less frequently, Cybersecurity Incident Response Team.
- CIRC stands for Computer Incident Response Center or Computer Incident Response Capability.
These terms are often used interchangeably in the industry, and since there is no formal standardization, we adopt CSIRT as it appears to be the most commonly used term today.
CSIRT or Computer Security Incident Response Team is an organizational entity (i.e., composed of one or more people) tasked with coordinating and supporting responses to a security event or incident.
The CSIRT and its acronym siblings can exist permanently and dedicatedly or be created ad hoc in response to an event. In either case, it is always focused on the four phases of responding to an incident (or security event, if a potential problem has been identified but not yet escalated to an incident):
- Preparation.
- Detection and analysis.
- Containment, eradication, and recovery.
- Post-incident activities to prevent recurrence.
SOC team responsibilities often encompass these tasks, in whole or in part.
At Looplex, we have a security operations team (SecOps) embedded within the development team to implement the integrated DevSecOps concept. Although the SecOps team has permanent responsibilities, we can also create CSIRT teams as needed, similar to how we form teams for legal engineering or development projects.
Thus, whenever an incident or potential incident is identified, we compose a CSIRT team to act on the aforementioned (a) preparation, (b) detection and analysis, (c) containment, eradication or mitigation, and recovery; (d) post-occurrence activities to strengthen our security and future prevention.
Case study: Creating the CSIRT at Looplex
This dynamic was exemplified in response to the news of a zero-day security vulnerability (i.e., no patch available yet) in the Java Spring Framework (CVE-2022-22965), which jeopardized millions of servers and applications worldwide.One of our members noticed the alert raised by the community—this event was so significant that it was published in traditional media worldwide—and on the same day, we assembled a CSIRT team to investigate whether we had any of the identified vulnerabilities.
The team consisted of SecOps members, the CTO, and a senior developer familiar with the potentially affected systems.
The response, fortunately, was negative; we did not use the compromised component anywhere in our stack, and thus, the vulnerability did not impact us. After defining preventive measures (blocking the use of the component in any future projects by unaware developers), which added another layer of security to our systems for similar events, the CSIRT team was disbanded, with its members resuming their daily activities.